Overview
This unique tool was developed by a client for internal use by their security team.
It provided code scanners a clear image of how vulnerability issues are being detected and prioritized during a scan process, and created a common narrative around how to configure scans to be more efficient.
Tool impact
As numerical data can't be shared, the impact of the tool on internal scanning processes was significant at:
Noise reduction (main tool objective)
As less false-positive vulnerability issues were created by each scan.
Reducing avg. scan time
Static scans were configured in a more informed way.
Contributing to overall scan execution policy
As the narrative became more solid, it helped optimizing the overall scan policy in the organization.
The problem
When scanning their code, the team was constantly dealing with scan results containing large amounts of false-positive vulnerability issues. Mostly due to frequent, major changes in the product, as well as the team itself, it was challenging to configure their SAST (Static Application Security Testing) scans in a way that will produce precise enough results, and considerable amounts of redundant work, as general routine.
The Solution
Context
To build better understanding of how scan configurations affect its results, we planned to improve the learning phase in the scan cycle.
retrospect within the scan cycle
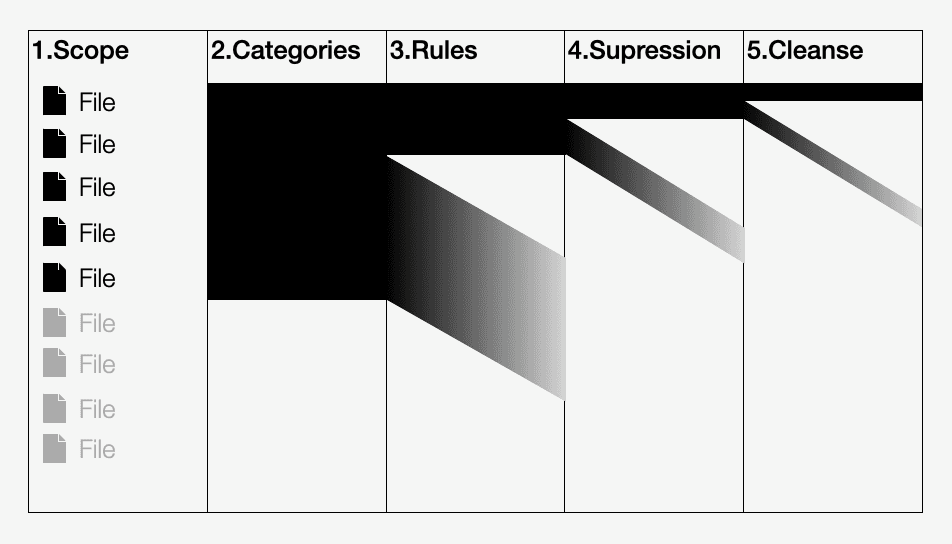
Data breakdown
One of the major challenges was structuring large amount of parameters into a coherent structure of an ordered funnel:
The static scan configurations were grouped by the different levels of their effect on vulnerability issues generation:
Static scan configuration process, as broken down for project purposes.
Layout
Based on the information architecture, horizontal layout was decided, to convey logical flow in a single glance.
Logic Declined: Nodes structure
The initial thought was of a node-structure presentation, to support simulations:
Logic Decided: Sankey Diagram
On the other hand, Sankey Diagram was better communicating causality and ratios, thus serving the original purpose:
Interface
General flow
showing the overall process of issues screening as a funnel.
Focus state
Focus state on partial classes and areas in the code.
Focus state
Filtering and sorting mechanisms for inspection and comparison.
Summary
The tool was active in internal use of the client for a bout 1-2 years and discontinued, partly due to shifts and changes in the company's work as and partly since more holistic, mature and robust solutions, available as part of existing AppSec tool offerings made it redundant.
Copyright © 2024 Avin Vadas. All rights reserved.